Researchers at Trend Micro are sounding the alarm against government-backed Chinese hackers. The hackers have been confirmed to be involved in targeted phishing campaigns that distribute customized malware stored on Google Drive. This malware is dropped on specific locations such as government networks, research sites and even academic organizations.
Also See: What is Hootsuite? How to Use it?
Attacks Peaked Between March and October
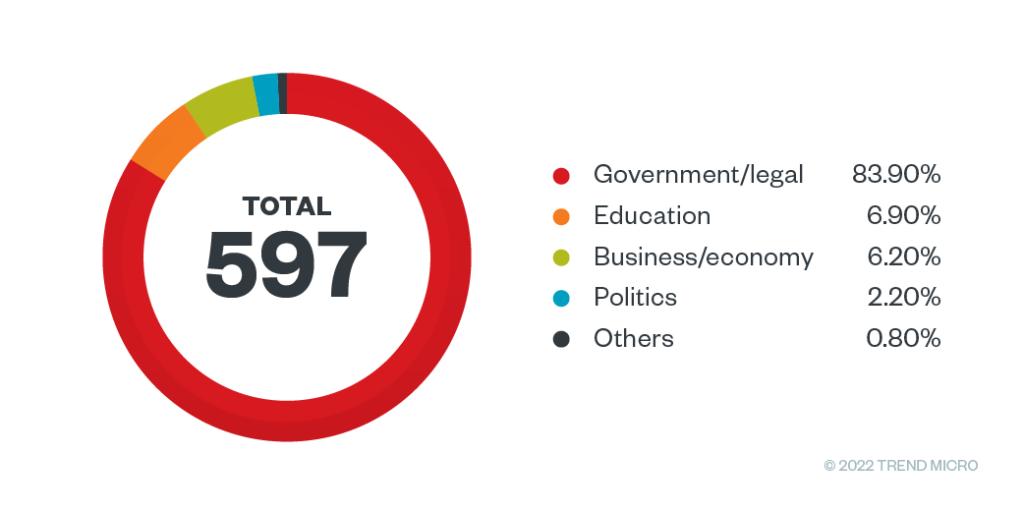
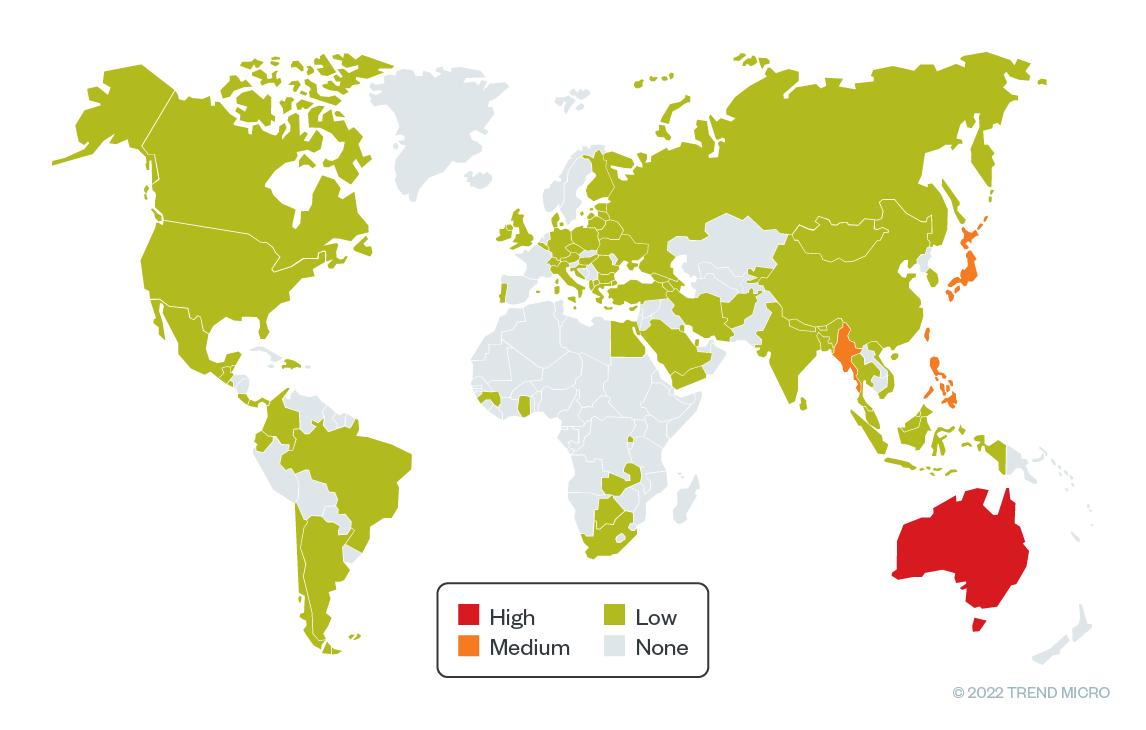
As Trend Micro researchers note, this threat group mostly targets organizations located in places like Australia, the Philippines, Taiwan and even Japan. You can also see that hackers are using built-in Google accounts to release targets in the emails. They are trying to convince victims to install custom malware via links from Google Drive.
More details have emerged about how most of the hackers used messages linked to geopolitical themes, revealing that most of the targets were government agencies. Since their links pointed to folders seen in Google Drive and even Dropbox, they bypassed all existing security mechanisms. Most of the links point to files that appear in compressed ZIP or RAR formats and contain various types of malware such as ToneShell and PubLoad.
The researchers also explain how the latest campaign has some of the Mustang Panda tactics that experts warned about in September this year. But this new campaign shows signs of having better toolkits and the ability to expand, resulting in an increased ability for hackers to gather intelligence details and even attack targets with ease.
At the beginning of 2022, another report by Proofpoint described how Mustang Panda focused on operations in Europe, targeting high-ranking diplomats. Meanwhile, another report published around the same time revealed a Mustang Panda attempt to target officials from Russia. Then, in March this year, Mustang Panda carried out operations in Southeast Asia, Africa and even the southern regions of Europe.





No comments yet for this news, be the first one!...